Introduction
Imagine a hacker being able to access data or resources on your customer’s sensitive information system just by changing a number in the URL—bypassing all authorization checks. This is the reality of Insecure Direct Object References (IDOR), a critical vulnerability that is commonly found in web applications. IDOR allows attackers to bypass authorization checks, expose personal data, manipulate accounts, and even cause financial losses.
What Is IDOR ?
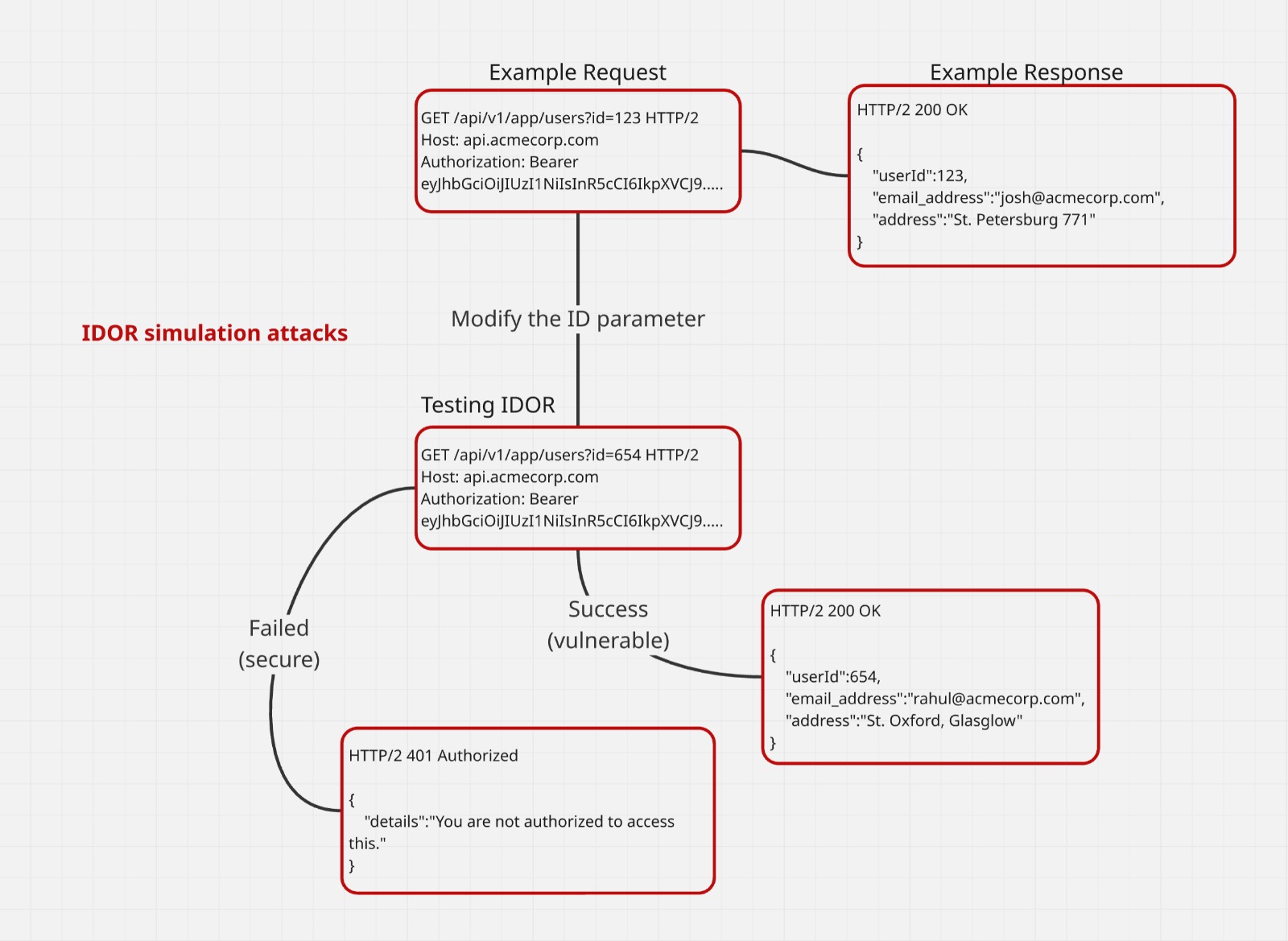
Insecure Direct Object Reference (IDOR) happens when a web application provides a reference or ID that users can use to access or modify information they’re not authorized to see. This usually happens when the app uses a direct reference to access certain data without properly verifying the user’s authorization.
One common example of IDOR is using a user ID. Many databases and website backends assign user IDs in ascending order—starting from 1 and above. This means, for example, that the account for user 8201 was created just before the account for user 8202.
This approach can create security issues for web applications. For example, if an app lets user 8201 access their account settings through the following web address:
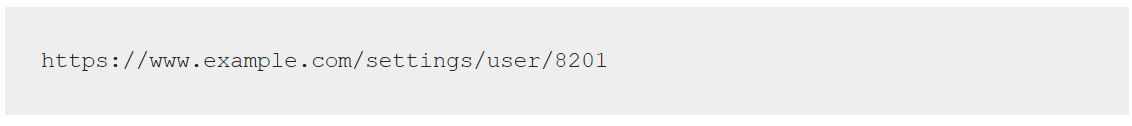
An attacker might figure out that the account settings for user 8202 could be available at:

This alone may not necessarily be an issue. An IDOR vulnerability occurs when a web application does not implement proper access controls. If the system does not correctly verify a user’s identity, an attacker may be able to freely view or even modify another user’s account settings.
A similar case often occurs in transactions, such as purchases or bookings. For example, if a user notices that their transaction ID is 19346, they might be able to access other transaction information (for example, 19345, 19347, and so on) simply by changing the ID number.
How We Identified IDOR Vulnerability for Your Company
Before we attempt a single attack, we first create a “blueprint” of your application. Our team systematically maps out every function and endpoint to identify all the places where the application uses identifiers (such as user IDs, invoice numbers, or filenames) to access data. We also analyze the various user roles that exist (such as standard users, managers, or administrators) to clearly understand who should have access to what data. This logic map forms the basis for recognizing any deviations from the intended access rules.
The goal is to find every location where user-supplied input is used to refer to objects directly. These potential areas include:
- Parameters in the URL query string (e.g., ?id=123 or ?file=report.pdf).
- Values in a POST request body or JSON payload (e.g., {“user_id”: 789}).
- Values in custom HTTP headers (e.g., X-User-ID: 123).
- Identifiers stored in session cookies.
With full vulnerability scanning access granted by our clients, we deliver proactive cybersecurity services that uncover hidden threats before attackers do. A website that appears perfectly secure can, in reality, be a prime target for black-hat hackers aiming to exploit weaknesses in your cloud security. Our continuous penetration testing ensures that every potential entry point is sealed—so you can protect your business from hackers before they strike.
How to Prevent Insecure Direct Object Reference (IDOR)
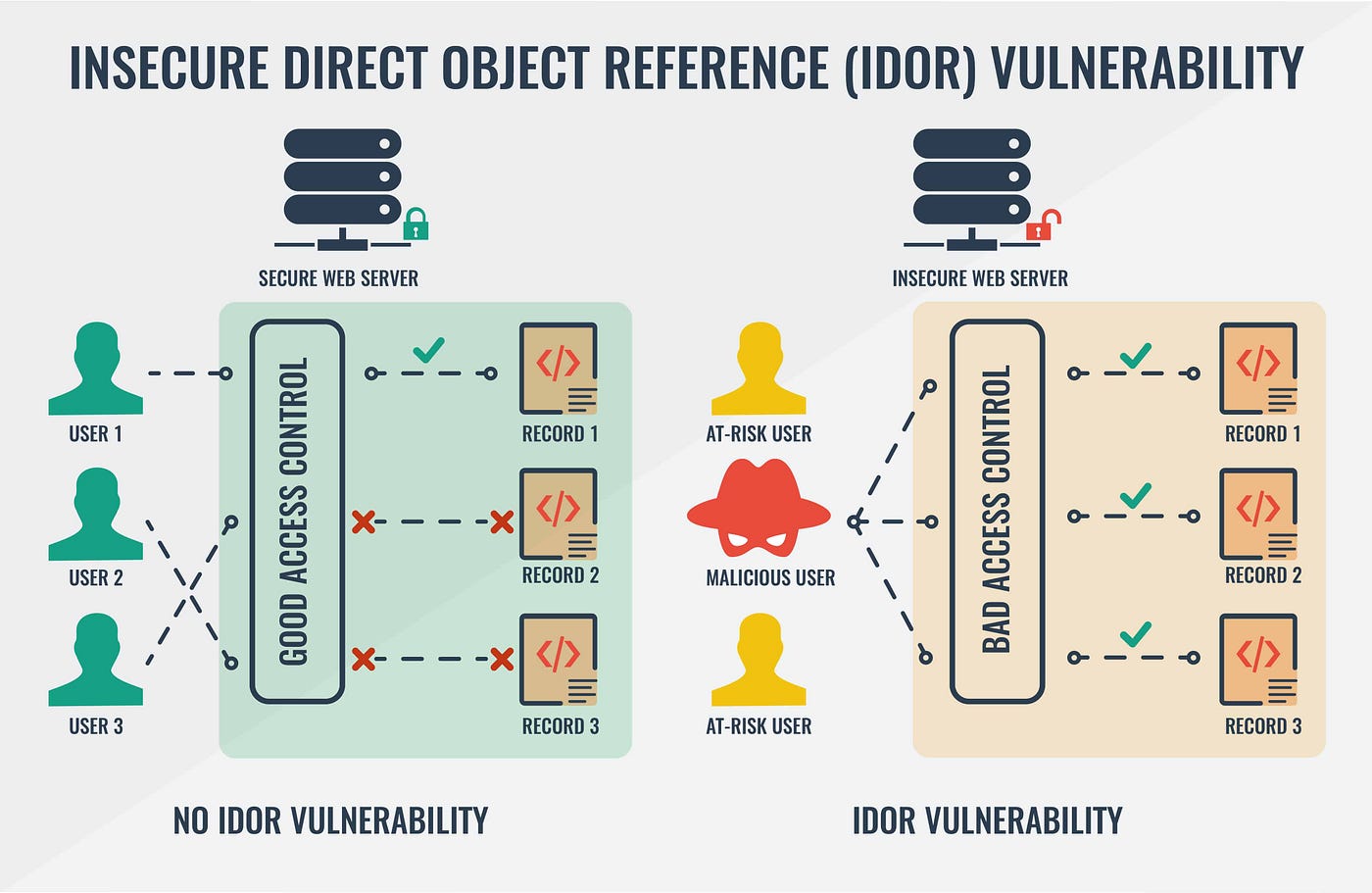
However, what they don’t realize is that Insecure Direct Object References (IDOR) vulnerabilities operate at the application logic level (a blind spot for WAF). The WAF, which serves as a general traffic filter, has no contextual understanding of the application’s business logic and cannot discern how user permissions should be applied to specific requests. This gap makes the system vulnerable to exploitation, as IDOR vulnerabilities allow attackers to manipulate direct references, such as IDs or parameters in URLs, to access unauthorized resources.
How the Expert see This (Abdan) Team SCS
“Many organizations underestimate the severity of logic-based vulnerabilities such as Insecure Direct Object Reference (IDOR). In this align, Sawah Cyber Security’s penetration testing program is engineered to surface and eliminate object-level authorization gaps before they can be exploited, combining threat modeling and data-flow mapping with context-aware tampering across REST, GraphQL, and WebSocket interfaces to validate and harden authorization logic.”


